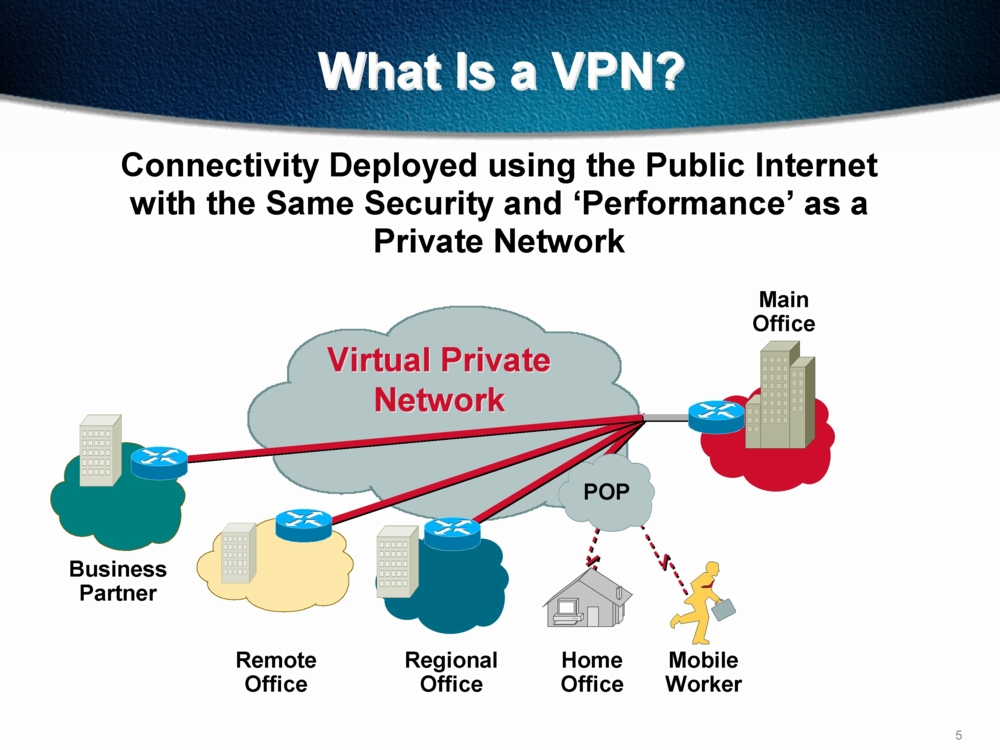
A VPN is a Virtual Private Network, which is service system where you can hide your internet IP address to browse the internet anonymously. It works in much the same way as a proxy, but rather than being used through your internet browser you can use it to hide every aspect of your online life; that is sharing files, watching videos and anything else that requires an internet connection.
The websites you visit will all be encrypted, so that nobody can see the websites you have been browsing and any other user data that is normally stored by your ISP (Internet Service Provider). However there are lots of things to consider and companies will always try to sell you their service, so here is what you should look out for.
Look at the location you will appear under
The best option is to go with a company which will allow you to choose your own location and change it every time you log in to the VPN. This is so that you can bypass laws which may restrict you in your own country; a lot of people use VPNs to bypass video blocks for online players in countries that they like to watch TV shows from, for example.
Some providers will provide you with one location, whereas others allow you to choose each time where you want to appear from. Make sure you know which deal you are getting so that you don’t pay money for a service you can’t use.
Know the Privacy Policy
In the world we live in today we are being watched by the government. In our homes, driving our cars and walking around the grocery store, we are always being monitored and records being logged of what we do. The same applies to the internet, and even with a VPN your online surfing may not be quite as anonymous as you think.
The United States and the United Kingdom work very closely together, with the CIA/NSA and MI6/GCHQ logging the internet habits of citizens around the world. For many years our “special relationship” has been for national defense, but now it seems that it’s being used to share internet logs.
You need to check whether the VPN holds any logs of what you do, and if they do whether they will release them to the federal government. Proxy websites in the past have been forced to hand over information by the courts, so check thoroughly whether logs will be kept; if there are logs of your activities, what you are doing is no longer anonymous and you may not wish to pay for a VPN. Companies do not have any choice but to hand over documents if they are requested by a court, unless they don’t actually keep any logs!
Ask about the VPN’s security
Request information about how strong the encryption process is on your VPN. Ask how many times the data is encrypted and if it can be decrypted. This is less about the government and more about the websites you are visiting; the federal government can more than likely see what you are doing, but you might not want a web master knowing your location and so security is very important.
A lot of the time people use VPNs to hide what they are doing from their ISP rather than the government – after all in many cases it is the ISP which will take you to court if they think you are breaking the law.
You will have to trust them
A great deal of trust has to exist between you and your VPN provider. What they say and what they actually do are very different things, so even if you are assured that no logs are kept you may find that in fact they record your every online movement. Don’t go with a company that you don’t trust, but also don’t place too much faith in a VPN company: after all they aren’t going to risk their company just to save your back.
Enquire about their policy
You should always ask them where they are based, and then do some research about the internet laws of that country. Many European countries are subject to EU law (although not all!) and so you should check whether they are part of international agreements about things such as internet tracking.
The worst countries for logging your activities are the United States, the United Kingdom and any countries with close diplomatic links including much of Europe. Most of these countries will have legislation which forces the VPN company to keep a log of what you are doing, even if said log is hidden from your view.
If you find that the company is not subject to such laws, ask whether they would dissolve the company or move it if similar laws were put in place. You won’t have a cast iron guarantee, but you will get an idea as to whether they can be trusted. If you suspect they are lying, avoid them – you might never find a company which is completely straight with you when it comes to the law, but you shouldn’t start out distrusting them.
This post is written by Kate Funk. She is a professional blogger and writer at www.tutorsville.net. She specializes in topics of interest to techno geeks and networking enthusiasts.
Virtual Private Networks For Dummies
Let’s face it: the information age makes dummies of us all at some point. One thing we can say for sure, though, about things related to the Internet is that their best strengths are often also their worst weaknesses. This goes for virtual private networks (VPNs).
They may reach a wide base of customers – but can also be vulnerable to viruses, hackers, spoofers, and other shady online characters and entities. VPNs may allow for super-efficient communication between customer and company – but they rely on information which, if compromised, can cause huge losses.
The Internet is still a frontier – sometimes so wide open it leaves us bewildered – and, like any frontier, the risks go hand in hand with potentially huge rewards.
Building Linux Virtual Private Networks (VPNs)
 Building Linux Virtual Private Networks (VPNs) covers the most popular VPN technologies available for the Linux platform. In the early chapters the theory behind VPNs is discussed, including needs and uses.
Building Linux Virtual Private Networks (VPNs) covers the most popular VPN technologies available for the Linux platform. In the early chapters the theory behind VPNs is discussed, including needs and uses.
Common network and host configurations are also covered. Subsequent chapters drill down into the implementation and configuration of specific software packages. Specific, detailed instructions are included as well as troubleshooting information.
This book will be an indispensable resource for anyone who wants to implement a Linux-based VPN. This book will meet the needs of anyone, from the Linux user to the experienced administrator to the security professional.
Building and Integrating Virtual Private Networks
 This book is a comprehensive guide to using Openswan for building both basic and industry size, military strength VPNs for medium to very large organizations. Written by the core developers, this practical book is all you need to use Openswan to build any VPN infrastructure you may need.
This book is a comprehensive guide to using Openswan for building both basic and industry size, military strength VPNs for medium to very large organizations. Written by the core developers, this practical book is all you need to use Openswan to build any VPN infrastructure you may need.
The authors have covered the latest developments and upcoming issues. This book will not only help you build the VPN you need, but also save you a lot of time. Network administrators and any one who is interested in building secure VPNs using Openswan. It presumes basic knowledge of Linux, but no knowledge of VPNs is required.






Thanks for sharing about VPN sevices which many people don’t know about.
Glad you like this post. Thanks for dropping your comment here.
I should also add that a VPN provider must have a kill switch and split-tunneling feature, therefore they can speed up their connection using split-tunneling and still secured if ever their connection fails because kill switch is enabled. I think this would help a lot of your readers, it certainly helped me 🙂